Who is attacking the healthcare industry?
Advancements in technology have offered healthcare an opportunity to save lives and operate efficiently. This technology has created vulnerabilities to threats that infiltrate, steal, or hijack networks of confidential data and systems. Whatever the reason for the threat, hospitals and medical facilities are targeted using a different variety of methods. Ransomware, phishing, and other nefarious software loaded into medical equipment, infiltrate networks that could potentially compromise patient data or hospital infrastructure.
Nation-states have used these opportunities to gather intelligence using software espionage tools and customized malware in social engineering attacks to steal intellectual property or gain competitive advantage. For instance, the second–largest healthcare insurance provider in the United States was affected by a foreign government attack in this way in 2014. Cyberterrorists, meanwhile, launch disruptive or destructive cyberattacks to cause physical destruction of property, loss of life and spread terror. Hacktivists are internet activists who attack cyber assets to draw attention to their political causes and tend to choose highly visible or high-profile targets. More recently, Cybersecurity Ventures predicts that the healthcare industry will spend more than $65B cumulatively on cybersecurity products and services over the five years from 2017 to 2021 as published in the 2020 Healthcare Cybersecurity Report.
Another category of possible attackers is the insider threat. Insider threats may be borne out of negligence, like opening a phishing email by mistake. Data privacy Patient and employee Personally Identifiable Information (PII), which includes patient diagnosis and treatment data, insurance and financial information, research and drug trial data, payroll, and intellectual property may be compromised in this way. Most of which could be minimized with a secure supply chain model and internal education of staff.
Why is the healthcare industry being attacked?
The key motivator for the vast majority of cyberattacks happens for monetary gain. Healthcare information is 10 times more valuable on the black market than social security numbers and credit card information. But in the healthcare world, not all perpetrators attacking healthcare providers will be motivated by money. Healthcare providers such as hospitals are highly visible targets and attacks against them will cause a major disruption in operations or threat to data housed within a hospital network. Disruptive attacks can disable, sabotage, or knock critical systems offline inside a hospital. The health and safety of vulnerable patients suffer as a result. Intellectual property, research data, drug trial data, PII, financial/ insurance data, medical records could be accessed and used in various ways.
The healthcare industry is a massive, complex, interconnected ecosystem with thousands of endpoints, systems, and users. The size, complexity, and functions of this ecosystem create large and oftentimes unpredictable attack surfaces. In a technical sense, threat actors can use several attack routes to infiltrate or sabotage a system.
How are they attacking the healthcare industry?
Entry points that threat actors can use to compromise the hospital supply chain range from manufacturers to distribution centers and transportation companies, from third-party contractors to developers of software and mobile apps hospitals use, from past to non-core services staff. (figure 1. image supply chain flow)
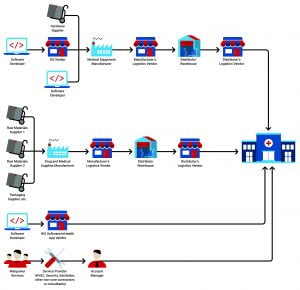 Figure 1.0 Supply Chain potential Risk access points
Figure 1.0 Supply Chain potential Risk access points
“Supply chain threats arise as a result of outsourcing suppliers, and the lack of verifiable physical and cybersecurity practices in place at the suppliers,” Sterling OEM, Trendmicro pointed out.
“Suppliers do not always vet personnel properly, especially companies that have access to patient data, hospital IT systems, or healthcare facilities. Vendors do not always vet their products and software for cybersecurity risk and maybe outsourcing resources as well.”
The following statistics from the HITRUST Cyber Threat XChange (CTX) program — a threat indicator sharing platform — show a few chosen markers about the healthcare industry cyber threat landscape that provide a snapshot about the most common infection vectors.
Other threats, as illustrated in Figure 2. are supplies, equipment, and software that come from unvetted sources. Education is key to procurement personnel to know that the supplier has been vetted to eliminate gray market equipment making its way into a hospital or medical facility. As a reseller, Sterling Sr. VP, Jeff Moore states in a recent article published by MeriTalk, “The bottom line is that facilities need comprehensive assessments of their suppliers to understand the total risk. Training procurement staff and buyers to look beyond the Bill of Materials (BOM) and the part number is essential.”
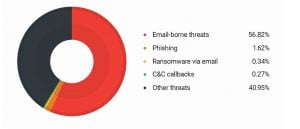
Figure 2. Distribution of Indicators of Compromise (IoC) types, 2017 Q4 (Source CTX Enhanced Pilot)
To date, the majority of publicly reported cyberattacks against hospitals have been one of the following:
- data breaches
- ransomware
- medical device compromise
Cybersecurity Ventures predicted that healthcare would suffer 2-3X more cyber-attacks in 2019 than the average amount for other industries with email fraud attacks increasing 473 percent in the last 2 years. Data breach costs will continue to worsen in 2020 according to the latest Black Book Survey research report.
As healthcare organizations grow, they increase in complexity. Without a secure supply chain, healthcare facilities may face more uncertainty. At the end of the day, healthcare facilities need to know their resellers. Moore and Sterling advocate fiercely to maintain a true secure supply chain. Sterling is O-TTPS Certified (Open Trusted Technology Provider Standard Certification), CMMC certified and has a detailed Supply Chain Risk Management (SCRM) plan in place so customers can be assured of secure product procurement
Healthcare Supply Chain transformation provides a future of uninterrupted operations without the compromise of security to medical, patient, and financial data and systems.
For more on Secure Supply Chain and Healthcare Security:
www.sterling.com/secure-supply-chain-blog
Ransomware Attacks in the First Half of 2020
